Data fuels business, but we also share a large amount of data even in our personal lives. Even the most benign communications, like chats, requests to stop by the store on your way home, and even memes or pet pictures, are considered data—and where there’s data, there’s a place where it’s stored. Today’s question: do you know where your data is being stored? And do you know the impact of that storage?
Human resources is not an easy game, as I’m sure your HR representatives would be happy to tell you if asked. Therefore, it is important that they have the tools needed for success today. By this, we mean information technology that supports the everyday responsibilities and processes that an HR department is charged with completing. Let’s discuss some tools that you should incorporate into your processes.
How many vendors are you managing? Probably quite a few. Now, think about how much time you spend on each one. What if you could reduce that time to almost nothing? We have some great news for you.
Potential data breaches pose a growing threat to organizations, with phishing attacks being the most prevalent method hackers use to steal sensitive information. It has become one of the most widespread online dangers, and understanding how it works is crucial to protecting your users. Let’s go into what phishing attacks are and explore some best practices to safeguard your network.
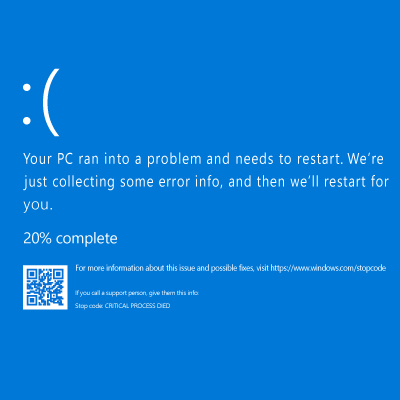
The recent CrowdStrike outage that disrupted many Microsoft-run systems has made headlines, even if it didn’t affect you directly. With so many organizations relying on Windows, this incident caused an unprecedented number of computer crashes, impacting over 8.5 million systems worldwide. The outage didn’t just cost businesses billions in lost revenue—it also led to the cancellation of 3,000 flights, throwing travel plans into chaos. As the largest outage in history, it served as a stark reminder that the technology we depend on daily isn’t foolproof. Today, we’ll explore key takeaways from the CrowdStrike outage and how businesses can better prepare for such events.
Email is undeniably a fantastic communication tool. However, there are certain things you should never share via email for safety reasons. Let’s explore what these are—because when it comes to security, it’s better to be safe than sorry.
The cloud has the potential to revolutionize a company’s operations in countless ways. Let’s explore the cloud and how it can support your operational goals and needs.
“Quit.” The q-word is often seen as one of the worst four-letter words in business. However, there are times when quitting can actually benefit your operations. Imagine you have a project consuming all your resources with no real returns. What should you do?
Google Drive is an extremely useful cloud storage and file sharing platform that many businesses use as a part of the Google Workspace productivity suite, or as a stand alone cloud storage solution. We thought it would be useful to give you a couple of ways to use Drive to share large files.
July 18th, 2024 saw one of the most widespread and devastating outages in recent memory, as a global update from cybersecurity company CrowdStrike brought about significant impacts to major infrastructures and societal needs. All this occurred even though only 1% of Windows operating systems experienced the issue.