Technology drives today’s businesses; if you haven’t embraced modern technology, you’re missing out. So much of what used to make business frustrating can now be done conveniently through technology, including many old analog tasks. Today, we want to highlight some ways you can use technology to seriously upgrade your company’s operations.
Businesses rely on a ton of technology for their operations and, as such, rely on support to help keep these tools working effectively. We would know! We proudly provide our neighbors with the technical assistance they need to succeed. As we’ve done so, we’ve noticed that there are some support needs we frequently attend to. Let’s review some of them and why they are so vital for you to have assistance in managing, preferably, from us!
Smart speakers have been around for a while now, but let’s be real… have they actually changed the world? Not really. They’re great for blasting music, setting reminders, and answering random trivia questions, but beyond that? Meh.
We all have old friends; not the ones that you went to high school with, but oldish technology that we simply can’t bring ourselves to upgrade away from. At some point, however, old technology stops being a trusty sidekick and starts feeling like an anchor. If your devices are making life harder instead of easier, it might be time to say goodbye. Here’s how to know when it’s time to let go and upgrade.
Skype is dead; long live Microsoft Teams. At least, that’s the position that Microsoft has taken. The software company is discontinuing the two-decade-old communication application Skype, shifting focus to the more recent Teams platform, with the app’s last day being scheduled for May 5. Let’s review what this means and reflect on Skype’s impact on modern technology.
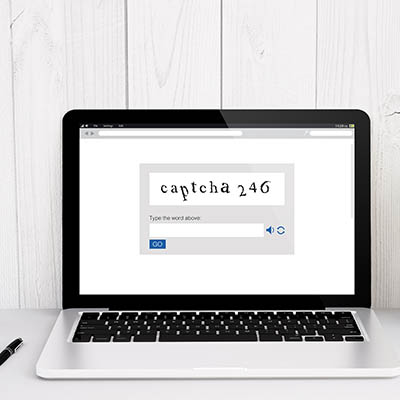
We’ve made it to the point where humans need to prove they’re real people to access systems, and one of the most common ways to do this is through the use of CAPTCHA technology. Completely Automated Public Turing test(s) to tell Computers and Humans Apart (try saying that with your mouth full) are everywhere, yet computers still struggle to actually crack these tests, unlike other methods of security. Why are they so successful at detecting automated bots?
We live in a moment in time defined by connectivity, which also means we live in a time defined by unwanted correspondence. It’s never been easier to reach you by phone, email, and even social media—even when you don’t want to be reached. Today, we’re talking about how social media, in particular, presents opportunities for scammers to target you and your loved ones.
Cybersecurity is one of those things everyone in a workplace should know about, no matter their role. But here’s the problem—turns out, a lot of people don’t. A recent survey in the UK found that about one in three adults flunked a cybersecurity test. And get this—the test was designed for 11-year-olds. Yikes.
Business is filled with situations that can easily be turned into problems if they are not met with a proper solution. In some cases, it’s as simple as changing a course of action, but some problems are deep-rooted and need to be addressed aggressively. Technology can often be a business’ saving grace in such instances. Let’s review some really bad scenarios that could be catastrophic, unless the right IT is in place.
Security is one of those things that every business owner worries about—no matter how big or small your company is. But the good news? It doesn’t have to be overwhelming. In fact, there are three simple steps you can take right now to make your business more secure.